Mastering IoT SSH Access On AWS: A Comprehensive Guide
Imagine this: you’ve built an IoT network, but now you need secure access to manage it remotely. That’s where IoT SSH access on AWS comes in, acting as your digital guardian. Whether you’re a developer or an IT professional, understanding how to securely connect to your IoT devices via SSH on AWS can be a game-changer. This isn’t just about setting up a connection; it’s about ensuring your data stays safe while giving you full control over your devices.
Let’s break it down. AWS offers robust tools to handle IoT SSH access, but navigating through the setup can feel like solving a puzzle if you’re new to the game. The good news? You’re in the right place. This guide will walk you through everything you need to know, from configuring SSH keys to managing secure connections, all while keeping your infrastructure protected.
So, buckle up! By the end of this article, you’ll have a solid understanding of IoT SSH access on AWS and how it can revolutionize the way you manage your IoT ecosystem. Let’s dive in!
- Alicia Rosenblumm Leaks The Untold Story You Need To Know About
- Unlocking The Mystery Of Xnxnxn Your Ultimate Guide To Understanding And Exploring
Table of Contents
- What is IoT SSH Access?
- AWS IoT Core: The Backbone of Your Network
- Why Use SSH on AWS?
- Setting Up IoT SSH Access on AWS
- Security Best Practices for IoT SSH Access
- Troubleshooting IoT SSH Connections
- Advanced Configurations for Enhanced Security
- Optimizing Performance for IoT SSH Access
- Real-World Use Cases and Examples
- Wrapping It Up: Next Steps for Your IoT Journey
What is IoT SSH Access?
Let’s start with the basics. IoT SSH access refers to using the Secure Shell (SSH) protocol to remotely connect to and manage IoT devices hosted on AWS. Think of SSH as a secure tunnel that allows you to interact with your devices without worrying about unauthorized access or data breaches.
SSH isn’t just about typing commands; it’s about creating a secure environment where you can troubleshoot issues, deploy updates, or monitor device performance from anywhere in the world. For IoT setups, this is crucial because devices are often deployed in remote locations, making physical access impractical.
And here’s the kicker: AWS provides the infrastructure and tools to make this process seamless. By integrating SSH with AWS services, you can manage your IoT ecosystem efficiently while maintaining top-notch security standards.
- Emily Compagno Relationships A Deep Dive Into Her Love Life And Connections
- Marjorie Taylor Greenes Children A Closer Look At The Family Life Of A Controversial Congresswoman
AWS IoT Core: The Backbone of Your Network
AWS IoT Core Defined
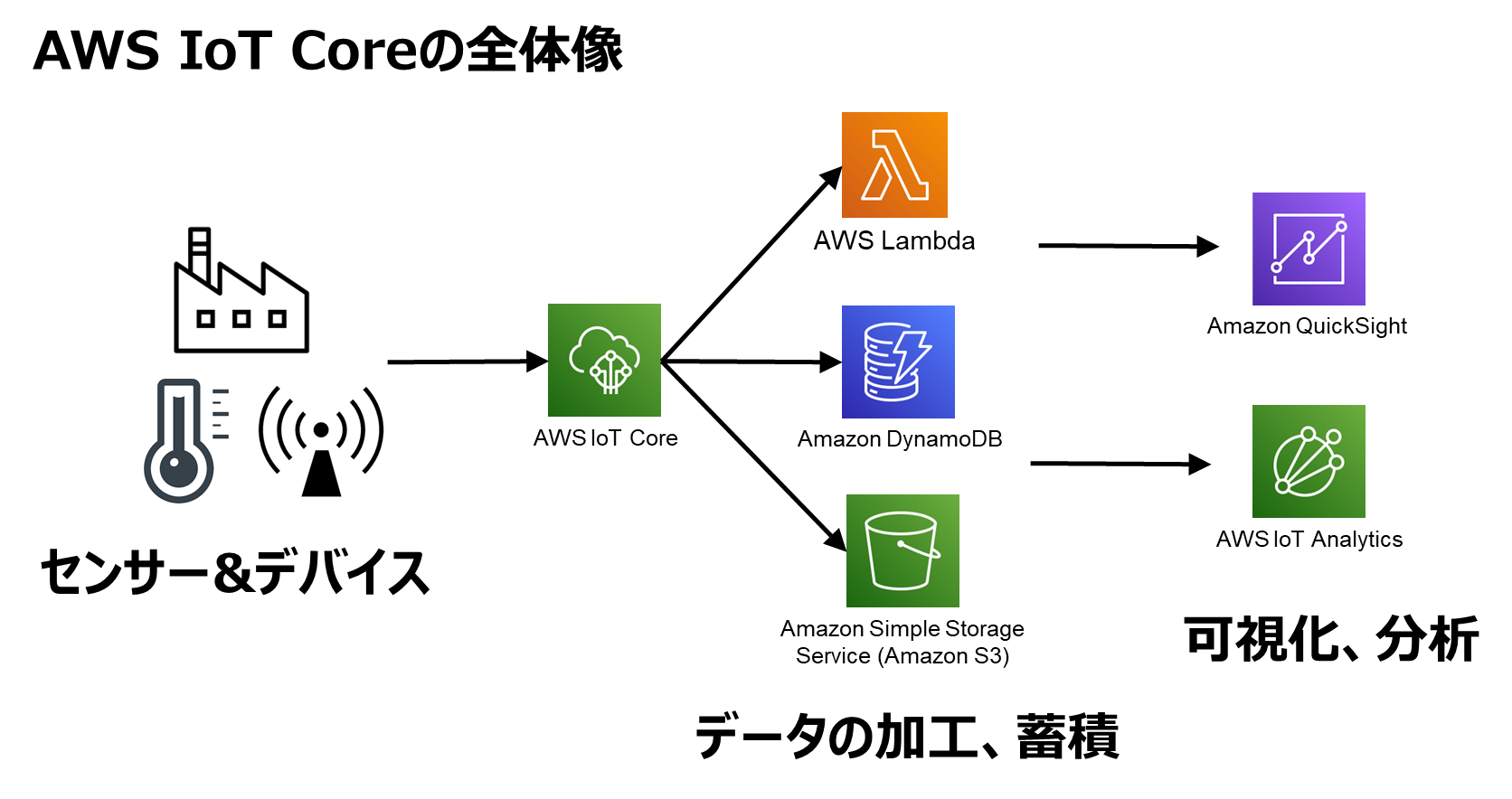
AWS IoT Core is the heart of your IoT infrastructure. It acts as a communication hub between your devices and the cloud, enabling secure and scalable interactions. With IoT Core, you can connect millions of devices and process trillions of messages—all while ensuring data integrity and security.
Here’s why AWS IoT Core is essential for SSH access:
- It simplifies device management by providing a centralized platform.
- It integrates seamlessly with other AWS services, such as Lambda and S3, for enhanced functionality.
- It offers robust security features, including device authentication and encryption, to protect your SSH connections.
In short, AWS IoT Core is the foundation that makes IoT SSH access on AWS possible.
Why Use SSH on AWS?
Now, you might be wondering, why bother with SSH when there are other ways to manage IoT devices? Well, here’s the deal: SSH offers unparalleled security and flexibility. Let’s break it down:
First, SSH encrypts all communication between your device and the server, making it nearly impossible for hackers to intercept sensitive data. Second, it allows you to execute commands remotely, giving you full control over your devices without needing physical access.
Plus, AWS enhances SSH’s capabilities by providing:
- Managed key pairs for secure authentication.
- Network-level security through VPCs and security groups.
- Monitoring tools to track SSH activity and detect potential threats.
In a world where cybersecurity threats are on the rise, using SSH on AWS is more than just a convenience—it’s a necessity.
Setting Up IoT SSH Access on AWS
Step 1: Create an IAM User
Before diving into SSH, you’ll need to set up an IAM user with the necessary permissions. This ensures that only authorized individuals can access your IoT devices.
Here’s how:
- Log in to the AWS Management Console.
- Navigate to the IAM service and create a new user.
- Assign the user the appropriate policies, such as "AWSIoTFullAccess" and "AmazonEC2FullAccess".
Step 2: Configure SSH Keys
SSH keys are the digital keys that unlock access to your devices. To set them up:
- Generate a key pair using the AWS EC2 console.
- Download the private key (.pem file) and store it securely.
- Associate the public key with your IoT device.
Step 3: Set Up Security Groups
Security groups act as virtual firewalls, controlling inbound and outbound traffic to your devices. To configure them:
- Create a new security group in the EC2 console.
- Allow SSH traffic (port 22) from your IP address or a specific range.
- Apply the security group to your IoT device.
With these steps, you’ll have a secure and functional SSH setup for your IoT devices on AWS.
Security Best Practices for IoT SSH Access
Security should always be your top priority when dealing with IoT SSH access. Here are some best practices to keep your setup safe:
- Use Strong Passwords: Even though SSH keys are the primary authentication method, ensure your IAM user passwords are complex and unique.
- Limit Access: Restrict SSH access to trusted IP addresses or ranges to reduce the risk of unauthorized access.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security by requiring 2FA for all SSH sessions.
- Regularly Update Software: Keep your devices and AWS services up to date to protect against vulnerabilities.
- Monitor Activity: Use AWS CloudTrail and CloudWatch to monitor SSH activity and detect any suspicious behavior.
By following these practices, you’ll significantly reduce the risk of security breaches and ensure your IoT ecosystem remains protected.
Troubleshooting IoT SSH Connections
Even with a well-configured setup, issues can arise. Here are some common problems and how to fix them:
Problem: Unable to Connect via SSH
Solution: Check your security group rules to ensure SSH traffic is allowed. Also, verify that your private key is correctly configured and matches the public key on the device.
Problem: Connection Drops Frequently
Solution: Investigate network instability or firewall settings that might be interrupting the connection. Consider increasing the timeout value in your SSH configuration.
Problem: Permission Denied Errors
Solution: Ensure your IAM user has the correct permissions and that the SSH key pair is properly set up. Double-check the file permissions for your private key.
With these troubleshooting tips, you’ll be able to quickly resolve most issues and maintain a stable SSH connection.
Advanced Configurations for Enhanced Security
If you’re looking to take your IoT SSH access on AWS to the next level, consider these advanced configurations:
1. Use Bastion Hosts
A bastion host acts as a gateway between your local network and AWS. By routing all SSH traffic through a bastion host, you can further secure your IoT devices and limit direct exposure to the internet.
2. Implement Role-Based Access Control (RBAC)
RBAC allows you to define granular permissions for different users and devices. This ensures that each user only has access to the resources they need, reducing the risk of accidental or malicious actions.
3. Enable SSH Logging
Logging SSH activity can help you identify potential security threats and troubleshoot issues more effectively. Use tools like AWS CloudWatch Logs to store and analyze SSH logs.
These advanced configurations can significantly enhance the security and functionality of your IoT SSH setup on AWS.
Optimizing Performance for IoT SSH Access
Performance optimization is key to ensuring your IoT devices respond quickly and efficiently. Here are some tips to improve performance:
- Compress Data: Use SSH’s built-in compression to reduce bandwidth usage and speed up data transfer.
- Optimize Network Settings: Configure your devices and AWS resources for optimal network performance.
- Use Caching: Implement caching mechanisms to reduce the load on your devices and improve response times.
By focusing on performance optimization, you’ll create a more responsive and reliable IoT ecosystem.
Real-World Use Cases and Examples
Let’s explore some real-world examples of IoT SSH access on AWS:
1. Smart Agriculture
Farmers use IoT devices to monitor soil moisture, temperature, and other environmental factors. With SSH access, they can remotely configure sensors and adjust settings to optimize crop growth.
2. Industrial Automation
In manufacturing plants, IoT devices are used to monitor machinery performance and predict maintenance needs. SSH allows engineers to troubleshoot issues and update firmware without visiting the site.
3. Smart Cities
IoT devices in smart cities collect data on traffic patterns, air quality, and energy consumption. SSH access enables city planners to analyze and manage this data from a centralized location.
These use cases demonstrate the versatility and power of IoT SSH access on AWS.
Wrapping It Up: Next Steps for Your IoT Journey
As we wrap up this comprehensive guide, let’s recap the key points:
- IoT SSH access on AWS provides secure and efficient remote management of IoT devices.
- AWS IoT Core serves as the backbone of your IoT infrastructure, offering scalability and security.
- Setting up SSH involves creating IAM users, configuring keys, and managing security groups.
- Security best practices and advanced configurations are essential for protecting your IoT ecosystem.
- Performance optimization ensures your devices respond quickly and reliably.
Now that you have a solid understanding of IoT SSH access on AWS, it’s time to take action. Whether you’re a developer, IT professional, or business owner, leveraging this technology can transform the way you manage your IoT devices.
So, what’s next? Start by experimenting with the setup process and exploring the advanced configurations we discussed. Share your experiences and insights in the comments below, and don’t forget to check out our other articles for more tips and tricks on IoT and AWS.
Remember, the future of IoT is here, and with AWS, the possibilities are endless. Happy coding, and stay secure!


Detail Author:
- Name : Edna Kautzer
- Username : baumbach.sharon
- Email : mcclure.vincent@yahoo.com
- Birthdate : 1987-04-14
- Address : 9240 Jast Junctions Suite 923 South Mabellestad, NH 24630-8611
- Phone : +1 (848) 691-8975
- Company : Marks-Hudson
- Job : Airline Pilot OR Copilot OR Flight Engineer
- Bio : Quas quo quia error voluptatem rerum sed aut sunt. Omnis non consequatur ab labore quod quia. Rerum ab omnis amet. Totam praesentium quaerat ex sunt. Expedita facilis enim quaerat sint cum quo.
Socials
tiktok:
- url : https://tiktok.com/@marlon944
- username : marlon944
- bio : Et nobis non voluptatum distinctio quisquam.
- followers : 4807
- following : 1641
twitter:
- url : https://twitter.com/marlonhaag
- username : marlonhaag
- bio : Sit impedit suscipit voluptatem. Consequuntur quisquam sunt dolorum maiores debitis veritatis.
- followers : 6555
- following : 1565
instagram:
- url : https://instagram.com/marlon67
- username : marlon67
- bio : Vitae qui eaque sed quaerat. Velit consequatur provident cumque dolor officiis suscipit.
- followers : 1972
- following : 1129
facebook:
- url : https://facebook.com/marlon_xx
- username : marlon_xx
- bio : Sed ea consequuntur quis hic officia sed ipsum.
- followers : 6913
- following : 1203
linkedin:
- url : https://linkedin.com/in/marlonhaag
- username : marlonhaag
- bio : Similique sed eligendi sed a animi magni vel.
- followers : 243
- following : 1659