Unlocking The Power Of RemoteIoT Platform SSH Key For Secure Connections
Let's talk about remoteIoT platform SSH key, shall we? If you're diving into the world of IoT or managing remote systems, understanding how SSH keys work within the remoteIoT ecosystem is crucial. This isn't just some fancy tech buzzword; it's a game-changer for secure communication. Imagine being able to control your IoT devices from anywhere in the world without worrying about hackers sniffing around your data. That's where SSH keys come into play. They're like digital bouncers at a super exclusive club—only letting the right people in.
Now, I know what you're thinking—"Why should I care about SSH keys?" Well, my friend, if you're dealing with remoteIoT platforms, these keys are your best bet for ensuring that your data stays safe and sound. Whether you're a tech enthusiast, a small business owner, or a big corporation, the importance of secure connections cannot be overstated. And trust me, once you get the hang of it, you'll wonder how you ever managed without them.
But hold up, before we dive deep into the nitty-gritty of remoteIoT platform SSH keys, let's take a moment to appreciate why security matters so much in today's digital landscape. With cyber threats lurking around every corner, having a solid security framework is no longer optional—it's a necessity. So, buckle up because we're about to embark on a journey to understand everything you need to know about SSH keys and how they can revolutionize your remoteIoT operations.
- Alice Rosenbluk Leaked Whatrsquos Really Going On And Why You Should Know
- Rosenblum Leaks The Inside Story Thatrsquos Making Waves Across The Globe
What Exactly is RemoteIoT Platform SSH Key?
Alright, let's break it down. The remoteIoT platform SSH key is essentially a cryptographic key pair used to authenticate users and devices when accessing remote servers or IoT devices. Think of it as a secret handshake that only you and the server understand. This key pair consists of a public key, which is shared with the server, and a private key, which you keep safely tucked away on your device.
Here's the cool part—when you try to connect to a remoteIoT server, the server checks your public key against the one it has stored. If they match, it sends you a challenge that only your private key can decrypt. Once decrypted, the server knows it's really you and grants access. It's like having a digital fingerprint that proves your identity without needing to type in a password every time.
Now, this might sound a bit complicated, but don't worry. Most remoteIoT platforms have user-friendly interfaces that make setting up SSH keys a breeze. Plus, once you've got it up and running, you'll never have to worry about remembering complex passwords again. And let's face it, who doesn't love a bit of convenience when it comes to security?
Why Use SSH Keys Over Passwords?
Let me tell you why SSH keys are way better than passwords. First off, passwords can be guessed, cracked, or even stolen through phishing attacks. SSH keys, on the other hand, are virtually impossible to crack. With a strong key length, the chances of someone brute-forcing their way into your account are astronomical.
Another advantage is that SSH keys eliminate the need for password entry every time you connect. Once you've set them up, you can seamlessly access your remoteIoT devices without typing in credentials. Plus, SSH keys can be further secured with passphrases, adding an extra layer of protection. It's like having a double lock on your front door—just in case.
Setting Up Your RemoteIoT Platform SSH Key
Setting up an SSH key for your remoteIoT platform is easier than you might think. Follow these simple steps, and you'll be good to go:
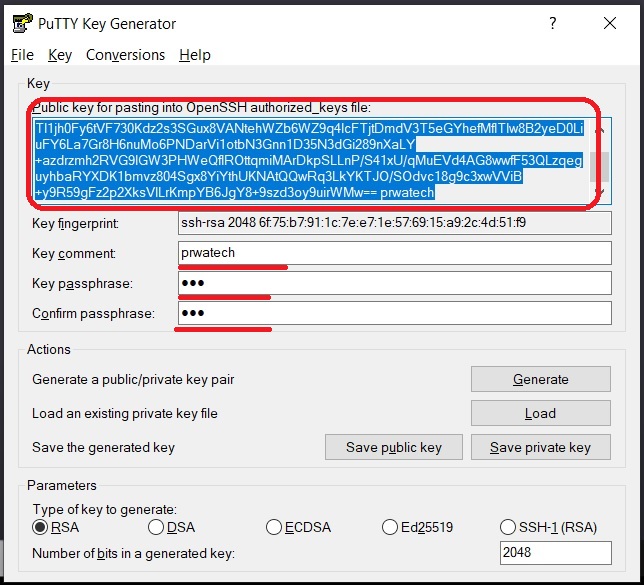
- Generate an SSH key pair using a tool like ssh-keygen on your local machine.
- Copy the public key to your remoteIoT server's authorized_keys file.
- Test the connection by trying to SSH into the server using your private key.
- Disable password authentication on the server to ensure only SSH key-based access is allowed.
It might sound like a lot, but most remoteIoT platforms provide detailed guides to help you through the process. And once you've got it set up, you'll wonder why you didn't do it sooner. Trust me, the peace of mind you get from knowing your connections are secure is priceless.
Tips for Generating Strong SSH Keys
Here are a few tips to ensure your SSH keys are as strong as they can be:
- Use a key length of at least 2048 bits for RSA keys or consider using Ed25519 for better performance and security.
- Protect your private key with a strong passphrase.
- Store your private key in a secure location and never share it with anyone.
By following these tips, you'll significantly reduce the risk of unauthorized access to your remoteIoT devices. Remember, security is all about layers, and SSH keys are just one piece of the puzzle.
Best Practices for Managing RemoteIoT Platform SSH Keys
Managing SSH keys effectively is crucial for maintaining the security of your remoteIoT platform. Here are some best practices to keep in mind:
- Regularly rotate your SSH keys to minimize the risk of exposure.
- Limit the number of people who have access to your private keys.
- Implement role-based access control to ensure only authorized users can access specific devices.
By adhering to these practices, you'll create a robust security framework that protects your remoteIoT operations from potential threats. And let's be honest, in today's digital world, you can never be too careful.
Common Pitfalls to Avoid
There are a few common mistakes people make when managing SSH keys. Here are some pitfalls to watch out for:
- Storing private keys in insecure locations, such as shared drives or unencrypted devices.
- Failing to revoke compromised keys promptly.
- Using weak or default passwords for key protection.
Avoiding these pitfalls will help ensure that your SSH keys remain a strong line of defense against unauthorized access.
Understanding SSH Key Authentication
SSH key authentication is the process by which a remoteIoT server verifies the identity of a user or device attempting to connect. This process involves several steps:
- The client sends its public key to the server.
- The server checks if the public key is authorized.
- If authorized, the server sends a challenge to the client.
- The client decrypts the challenge using its private key and sends the response back to the server.
- The server verifies the response and grants access if it matches.
This entire process happens behind the scenes, ensuring that your connection is secure without requiring you to enter a password every time. It's like having a silent bodyguard watching over your data.
Advantages of SSH Key Authentication
There are several advantages to using SSH key authentication for your remoteIoT platform:
- Increased security due to the cryptographic nature of SSH keys.
- Convenience of not having to enter passwords repeatedly.
- Ability to revoke access by simply removing the public key from the server.
These advantages make SSH key authentication a no-brainer for anyone serious about securing their remoteIoT operations.
Securing Your RemoteIoT Platform with SSH Keys
Securing your remoteIoT platform with SSH keys involves more than just setting them up. You also need to ensure that your server configurations are properly secured. Here are some tips:
- Disable password authentication entirely and rely solely on SSH keys.
- Use firewall rules to restrict access to your server from specific IP addresses.
- Regularly update your server software to patch any security vulnerabilities.
By taking these steps, you'll create a robust security environment that protects your remoteIoT platform from potential threats. Remember, security is an ongoing process, not a one-time event.
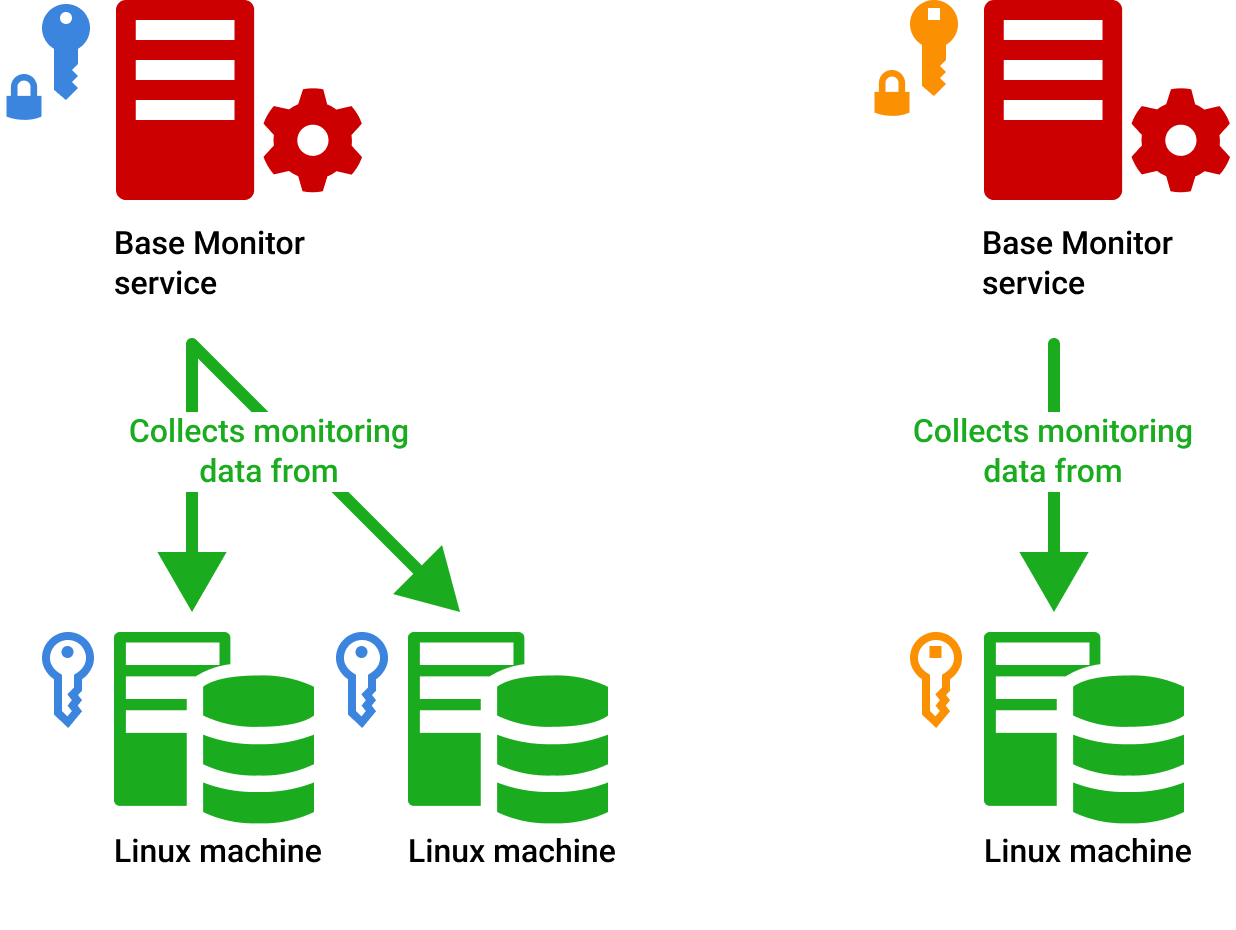
Monitoring SSH Key Usage
Monitoring SSH key usage is essential for maintaining the security of your remoteIoT platform. Here's how you can do it:
- Regularly review the authorized_keys file to ensure only valid keys are present.
- Implement logging to track SSH key usage and detect any suspicious activity.
- Set up alerts for unauthorized access attempts.
By keeping a close eye on SSH key usage, you'll be able to quickly identify and respond to any security threats that may arise.
SSH Key Management Tools for RemoteIoT Platforms
There are several tools available to help you manage SSH keys for your remoteIoT platform. Some popular ones include:
- SSH Key Manager by Atlassian
- HashiCorp Vault
- Keybase
These tools offer features such as key rotation, access control, and auditing capabilities, making it easier to manage SSH keys across multiple devices and users. Plus, they integrate seamlessly with most remoteIoT platforms, ensuring a smooth and secure experience.
Choosing the Right SSH Key Management Tool
When choosing an SSH key management tool, consider the following factors:
- Compatibility with your remoteIoT platform.
- ease of use and user interface.
- Security features offered by the tool.
Selecting the right tool can make a significant difference in how effectively you manage your SSH keys and secure your remoteIoT operations.
Future Trends in RemoteIoT Platform SSH Key Security
As technology continues to evolve, so do the methods for securing remoteIoT platforms. Here are some future trends to watch out for:
- Increased adoption of quantum-resistant algorithms for SSH keys.
- Integration of biometric authentication with SSH key management.
- Advancements in machine learning for detecting and preventing unauthorized SSH key usage.
Staying ahead of these trends will ensure that your remoteIoT platform remains secure in the face of ever-evolving cyber threats.
Preparing for the Future of SSH Key Security
To prepare for the future of SSH key security, consider the following:
- Stay informed about the latest developments in cryptographic algorithms.
- Invest in tools and technologies that offer advanced security features.
- Continuously educate yourself and your team about best practices for SSH key management.
By taking these steps, you'll be well-equipped to handle whatever the future of remoteIoT platform security throws your way.
Conclusion
So there you have it, everything you need to know about remoteIoT platform SSH keys. From understanding what they are to setting them up and managing them effectively, we've covered it all. Remember, security is not something you can take lightly, especially when dealing with remoteIoT platforms. By using SSH keys, you're taking a significant step towards securing your operations and protecting your data.
Now, here's the thing—I want you to take action. Whether it's setting up SSH keys for your remoteIoT platform or exploring the various management tools available, don't just sit there. Get out there and make your digital world a safer place. And if you found this article helpful, don't forget to share it with your friends and colleagues. Together, we can create a more secure future for everyone.
Until next time, stay safe and keep those SSH keys strong!
Table of Contents
- What Exactly is RemoteIoT Platform SSH Key?
- Why Use SSH Keys Over Passwords?
- Setting Up Your RemoteIoT Platform SSH Key
- Best Practices for Managing RemoteIoT Platform SSH Keys
- Understanding SSH Key Authentication
- Securing Your RemoteIoT Platform with SSH Keys
- SSH Key Management Tools for RemoteIoT Platforms
- Future Trends in RemoteIoT Platform SSH Key Security
- Preparing for the Future of SSH Key Security
- Conclusion

Detail Author:
- Name : Emilia Huel V
- Username : johnson.swaniawski
- Email : tyshawn42@rippin.com
- Birthdate : 1993-04-13
- Address : 547 Malvina Plain Wunschchester, IN 07229
- Phone : 1-283-507-5315
- Company : Kassulke, Waelchi and Crooks
- Job : Preschool Teacher
- Bio : Animi optio adipisci qui ut. Eaque accusamus inventore ut et et. Totam earum sed reprehenderit soluta laudantium. Consequatur temporibus vel quia et.
Socials
linkedin:
- url : https://linkedin.com/in/lkoepp
- username : lkoepp
- bio : Quae qui qui facilis qui quasi.
- followers : 3322
- following : 2954
instagram:
- url : https://instagram.com/ludie8139
- username : ludie8139
- bio : Ut at pariatur magni eveniet ut est. Dolores beatae explicabo expedita at saepe.
- followers : 1954
- following : 2867