Revolutionizing Connectivity: The Ultimate Guide To RemoteIoT Platform SSH Key
Hey there, tech enthusiasts! Are you ready to dive deep into the world of secure remote access? If you've been exploring ways to enhance your IoT network's security, you've probably stumbled upon the term "remoteIoT platform SSH key." This powerful tool is more than just a buzzword; it's your gateway to a secure, seamless connection between devices. Whether you're managing a smart home or running a large-scale industrial IoT setup, understanding SSH keys is crucial. Let's break it down step by step.
In today's hyper-connected world, security is everything. As IoT devices continue to grow exponentially, so does the risk of unauthorized access. That's where the remoteIoT platform SSH key comes in. It acts as a digital lock-and-key system, ensuring that only authorized users can access your devices. This guide will walk you through everything you need to know about SSH keys, from the basics to advanced configurations.
Before we jump into the nitty-gritty, let's set the stage. This article isn't just about theoretical knowledge; it's about empowering you with practical skills. By the end of this read, you'll be equipped to secure your IoT network like a pro. So, grab your favorite beverage, get comfy, and let's get started!
- Lara Rose Leaked The Untold Story Behind The Viral Sensation
- Mckinley Richardson Onlyfans Review A Comprehensive Look At Whatrsquos Worth The Hype
What Exactly is a RemoteIoT Platform SSH Key?
Alright, let's start with the basics. An SSH key is essentially a pair of cryptographic keys used to authenticate users in a secure shell (SSH) connection. In the context of remoteIoT platforms, these keys are critical for ensuring that only trusted devices and users can interact with your IoT network. Think of it as a digital handshake that verifies identities before granting access.
Here’s why SSH keys are a game-changer:
- They eliminate the need for passwords, reducing the risk of brute-force attacks.
- They provide a higher level of encryption compared to traditional password authentication.
- They simplify the management of multiple devices, making it easier to scale your IoT network.
For those of you who are new to the concept, don't worry. We'll break it down further in the upcoming sections. But for now, just remember that SSH keys are your best bet for securing remote access to IoT devices.
- Alice Rosenblum Leaked Photos The Truth Behind The Controversy
- Sandra Blust Erome The Untold Story Behind The Viral Sensation
Why Use SSH Keys for Your RemoteIoT Platform?
Now that we know what SSH keys are, let's talk about why they're so important for remoteIoT platforms. In the IoT ecosystem, security breaches can have devastating consequences. From unauthorized access to data theft, the risks are real. SSH keys help mitigate these risks by providing a robust layer of security.
Here are some compelling reasons to use SSH keys for your remoteIoT platform:
- Enhanced Security: SSH keys use strong encryption algorithms, making them nearly impossible to crack.
- Convenience: Once set up, SSH keys allow for seamless, password-less access to your devices.
- Scalability: Managing SSH keys across multiple devices is far easier than juggling dozens of passwords.
Imagine a scenario where your IoT network consists of hundreds of devices. Without SSH keys, managing access would be a logistical nightmare. But with SSH keys, you can streamline the process and focus on more important tasks.
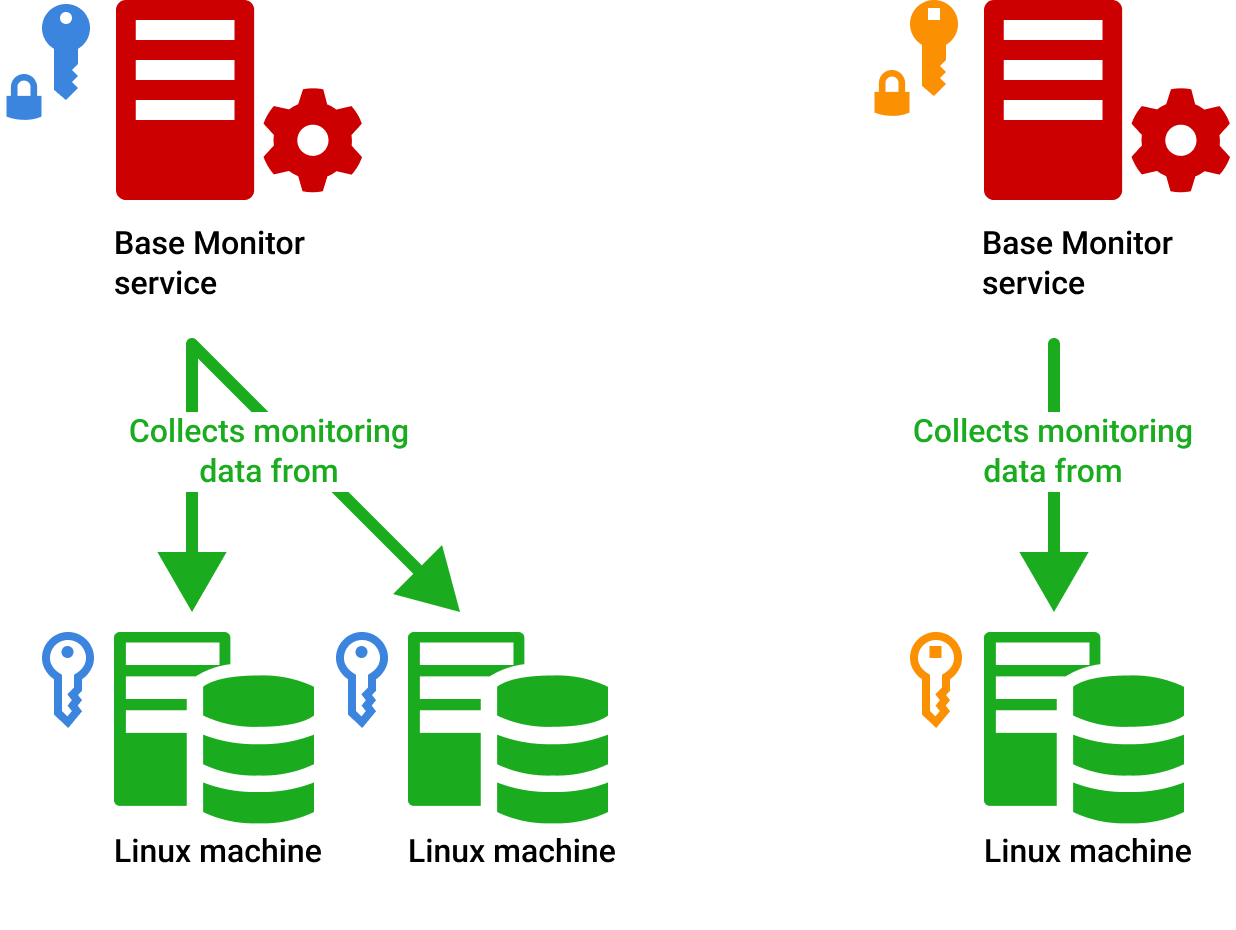
Understanding SSH Key Pairs
Let's take a closer look at how SSH key pairs work. Every SSH key consists of two parts: a public key and a private key. The public key is, well, public. It can be shared freely and is stored on the devices you want to access. The private key, on the other hand, is your secret weapon. It must be kept secure and never shared with anyone.
When you attempt to connect to a device using SSH, the public key on the device matches with your private key. If the keys match, access is granted. If not, access is denied. Simple, right? But don't let the simplicity fool you—this system is incredibly secure.
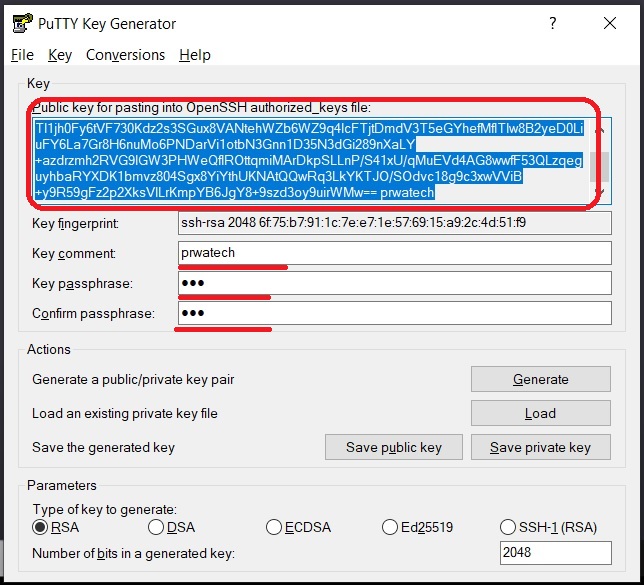
How to Generate SSH Keys for Your RemoteIoT Platform
Generating SSH keys is easier than you might think. Here's a step-by-step guide to help you get started:
- Open your terminal or command prompt.
- Type the following command:
ssh-keygen -t rsa -b 4096. This generates a strong RSA key pair with 4096 bits of encryption. - When prompted, specify a file location for your keys. The default location is usually fine.
- Set a passphrase for your private key. This adds an extra layer of security.
Voila! You now have a public and private SSH key pair ready to secure your remoteIoT platform.
Best Practices for Managing SSH Keys
Now that you know how to generate SSH keys, let's talk about managing them effectively. Proper key management is essential to maintaining the security of your remoteIoT platform. Here are some best practices to follow:
- Limit Key Distribution: Only share public keys with trusted devices and users.
- Use Strong Passphrases: Protect your private keys with strong, unique passphrases.
- Regularly Rotate Keys: Replace old keys with new ones periodically to minimize the risk of compromise.
- Monitor Key Usage: Keep an eye on which keys are being used and by whom.
By following these practices, you can ensure that your SSH keys remain a reliable security measure for your remoteIoT platform.
Common Misconceptions About SSH Keys
There are a few misconceptions about SSH keys that we need to address. One common myth is that SSH keys are only for advanced users. While they do require a bit of technical know-how, anyone can learn to use them with a little practice. Another misconception is that SSH keys are infallible. While they are incredibly secure, no system is completely immune to attack. That's why it's important to combine SSH keys with other security measures.
Here are some facts to set the record straight:
- SSH keys are not just for server admins; they're for anyone who values security.
- They can be used on a variety of devices, not just servers.
- While they are highly secure, they should be part of a broader security strategy.
Addressing Security Concerns
Security is a top priority for any remoteIoT platform. That's why it's crucial to address potential concerns head-on. For example, what happens if someone gets hold of your private key? This is where passphrases and key rotation come into play. By adding a passphrase to your private key and regularly updating your keys, you can minimize the risk of unauthorized access.
Real-World Applications of SSH Keys in RemoteIoT Platforms
So, how are SSH keys being used in the real world? Let's take a look at some examples:
- Smart Homes: SSH keys are used to secure connections between smart devices, ensuring that only authorized users can control them.
- Industrial IoT: In manufacturing, SSH keys protect critical infrastructure from cyberattacks.
- Healthcare IoT: Hospitals use SSH keys to secure medical devices, safeguarding patient data.
These examples illustrate the versatility and importance of SSH keys in various industries. Whether you're managing a small network or a large-scale operation, SSH keys have a role to play.
Troubleshooting SSH Key Issues
Even the best-laid plans can hit a snag. If you're having trouble with your SSH keys, here are some troubleshooting tips:
- Check Key Permissions: Ensure that your private key has the correct file permissions.
- Verify Key Placement: Make sure your public key is correctly placed on the target device.
- Test the Connection: Use the
sshcommand to test your connection and identify any issues.
Remember, troubleshooting is all about patience and persistence. If one solution doesn't work, try another until you find the root cause.
Advanced Tips for Power Users
For those of you who want to take your SSH key management to the next level, here are some advanced tips:
- Use SSH Agents: SSH agents streamline the process of managing multiple keys.
- Implement Key Revocation: Have a plan in place to revoke compromised keys quickly.
- Explore SSH Config Files: Customize your SSH settings for maximum efficiency.
These tips will help you optimize your SSH key setup and make the most of this powerful tool.
Conclusion: Securing Your Future with SSH Keys
And there you have it—a comprehensive guide to remoteIoT platform SSH keys. From understanding the basics to mastering advanced techniques, you're now equipped to secure your IoT network like a pro. Remember, security is an ongoing process. Stay informed, stay vigilant, and don't hesitate to reach out if you have questions.
Before you go, here's a quick recap of the key points we covered:
- SSH keys are essential for securing remote access to IoT devices.
- They provide enhanced security, convenience, and scalability.
- Proper key management is crucial for maintaining security.
Now it's your turn to take action. Whether it's generating your first SSH key or fine-tuning your existing setup, the choice is yours. And don't forget to share this article with your fellow tech enthusiasts. Together, we can build a safer, more connected world!
Table of Contents
What Exactly is a RemoteIoT Platform SSH Key?
Why Use SSH Keys for Your RemoteIoT Platform?
How to Generate SSH Keys for Your RemoteIoT Platform
Best Practices for Managing SSH Keys
Common Misconceptions About SSH Keys
Real-World Applications of SSH Keys in RemoteIoT Platforms
Troubleshooting SSH Key Issues

Detail Author:
- Name : Kitty Zulauf
- Username : donnie05
- Email : herzog.raven@mclaughlin.com
- Birthdate : 1990-12-25
- Address : 329 Jaleel Ridge North Ashlee, ID 03526
- Phone : 417.751.4182
- Company : Cummings PLC
- Job : Preschool Teacher
- Bio : Commodi omnis fuga recusandae illum ea maiores. Accusamus quidem non assumenda vitae fugit quae vel sit. Esse quidem sit animi non sint aut.
Socials
tiktok:
- url : https://tiktok.com/@alysa_upton
- username : alysa_upton
- bio : Aliquid non numquam omnis soluta earum unde non.
- followers : 6823
- following : 1531
twitter:
- url : https://twitter.com/alysa_real
- username : alysa_real
- bio : Veritatis animi aut aliquam velit nulla itaque. Nihil autem reprehenderit iusto. Voluptatibus tempora sunt sit aut non.
- followers : 1305
- following : 1405
linkedin:
- url : https://linkedin.com/in/alysaupton
- username : alysaupton
- bio : Dolores commodi culpa a nesciunt.
- followers : 3897
- following : 879
facebook:
- url : https://facebook.com/alysa_upton
- username : alysa_upton
- bio : Quasi a impedit non nobis enim. Sunt perferendis et nostrum.
- followers : 394
- following : 735
instagram:
- url : https://instagram.com/upton1986
- username : upton1986
- bio : Minus dicta voluptatem cupiditate. Neque dolores est at consequatur et quo.
- followers : 3506
- following : 569