IoT SSH Applications: Revolutionizing Connectivity And Security
Imagine a world where every device you own is interconnected, seamlessly communicating with one another, all while staying secure. That's exactly what IoT SSH applications are bringing to the table. Whether it's your smart fridge, thermostat, or security camera, these applications are transforming how we interact with technology in our daily lives. But what exactly are IoT SSH applications, and why should you care? Let's dive in!
So, here’s the deal. The Internet of Things (IoT) is no longer just a buzzword—it’s a reality that’s reshaping industries and homes alike. With billions of devices connected globally, ensuring secure communication between them has become a top priority. Enter SSH (Secure Shell), the superhero of secure data transfer. Combining IoT with SSH creates a powerful duo that’s set to redefine how we approach smart technology.
But hold up—this isn’t just about gadgets. It’s about creating a safer, smarter future where you can trust your devices to work together without compromising your privacy. Whether you’re a tech enthusiast or someone who simply wants to understand the tech behind your smart home, this article is here to break it all down for you. So grab a coffee, sit back, and let’s explore the ins and outs of IoT SSH applications!
- Wasmo Somali Telegram 2020 A Deep Dive Into The Phenomenon
- Alyx Star Nationality The Untold Story Behind The Global Sensation
What Are IoT SSH Applications?
Alright, let’s get into the nitty-gritty. IoT SSH applications refer to the integration of Secure Shell protocols within IoT ecosystems. Think of SSH as the bodyguard of your data, ensuring that everything transmitted between devices remains encrypted and secure. In the world of IoT, where countless devices communicate over networks, having a secure channel is non-negotiable.
Now, here’s the kicker: SSH isn’t new. It’s been around for decades, protecting server communications and remote access. But when you pair it with IoT, you unlock a whole new level of functionality. These applications allow devices to exchange information securely, whether it’s a smart lock updating its status or a drone sending live footage to your smartphone.
Let’s break it down further with some examples:
- Camilla Araujos Job On Onlyfans A Comprehensive Guide
- Hannah Barron Nudes Leaked The Truth Behind The Headlines
- Smart home systems using SSH to encrypt communication between devices.
- Industrial IoT setups where machines send encrypted data to central servers.
- Healthcare devices transmitting patient data securely to cloud platforms.
In short, IoT SSH applications are the glue that holds together the security and functionality of connected devices. And trust me, in a world where data breaches are a constant threat, this glue is pretty darn important.
Why Are IoT SSH Applications Important?
Here’s the thing: without security, the IoT revolution would grind to a halt. Imagine your smart home being hacked, or sensitive industrial data falling into the wrong hands. Scary, right? That’s where IoT SSH applications come in. They provide a robust layer of protection that ensures your devices aren’t just smart—they’re safe too.
Let’s talk numbers for a sec. According to a recent report by Gartner, there will be over 25 billion connected devices by 2025. That’s a lot of devices, and a lot of potential entry points for cybercriminals. SSH applications help mitigate this risk by encrypting data at both ends of the communication channel.
Here’s another angle to consider: compliance. In industries like healthcare and finance, data security isn’t just a nice-to-have—it’s a must-have. IoT SSH applications ensure that businesses can meet regulatory requirements while still leveraging the benefits of connected technology.
Key Benefits of IoT SSH Applications
Now that we’ve covered why these applications are so crucial, let’s look at some of the key benefits they bring to the table:
- Enhanced Security: With end-to-end encryption, SSH ensures that data remains safe from prying eyes.
- Scalability: Whether you’re managing a few devices or thousands, SSH applications can handle it all.
- Reliability: SSH protocols are battle-tested and proven to work even in challenging network conditions.
- Cost-Effective: By reducing the risk of data breaches, businesses can save money on potential fines and reputational damage.
These benefits make IoT SSH applications a no-brainer for anyone looking to build a secure and scalable IoT ecosystem.
How Do IoT SSH Applications Work?
Alright, let’s talk tech. At its core, an IoT SSH application works by establishing a secure connection between two devices. This is done using public-key cryptography, where each device has a unique key pair. When one device wants to communicate with another, it sends an encrypted message using the recipient’s public key. The recipient can then decrypt the message using their private key.
Here’s a step-by-step breakdown of the process:
- The initiating device generates a public-private key pair.
- It sends its public key to the receiving device.
- The receiving device uses the public key to encrypt data before sending it back.
- The initiating device decrypts the data using its private key.
Simple, right? Well, maybe not so simple, but it’s an incredibly effective way to ensure secure communication. And the best part? This process happens in the background, so you don’t even have to think about it.
Common Use Cases for IoT SSH Applications
Let’s take a look at some real-world examples of how IoT SSH applications are being used:
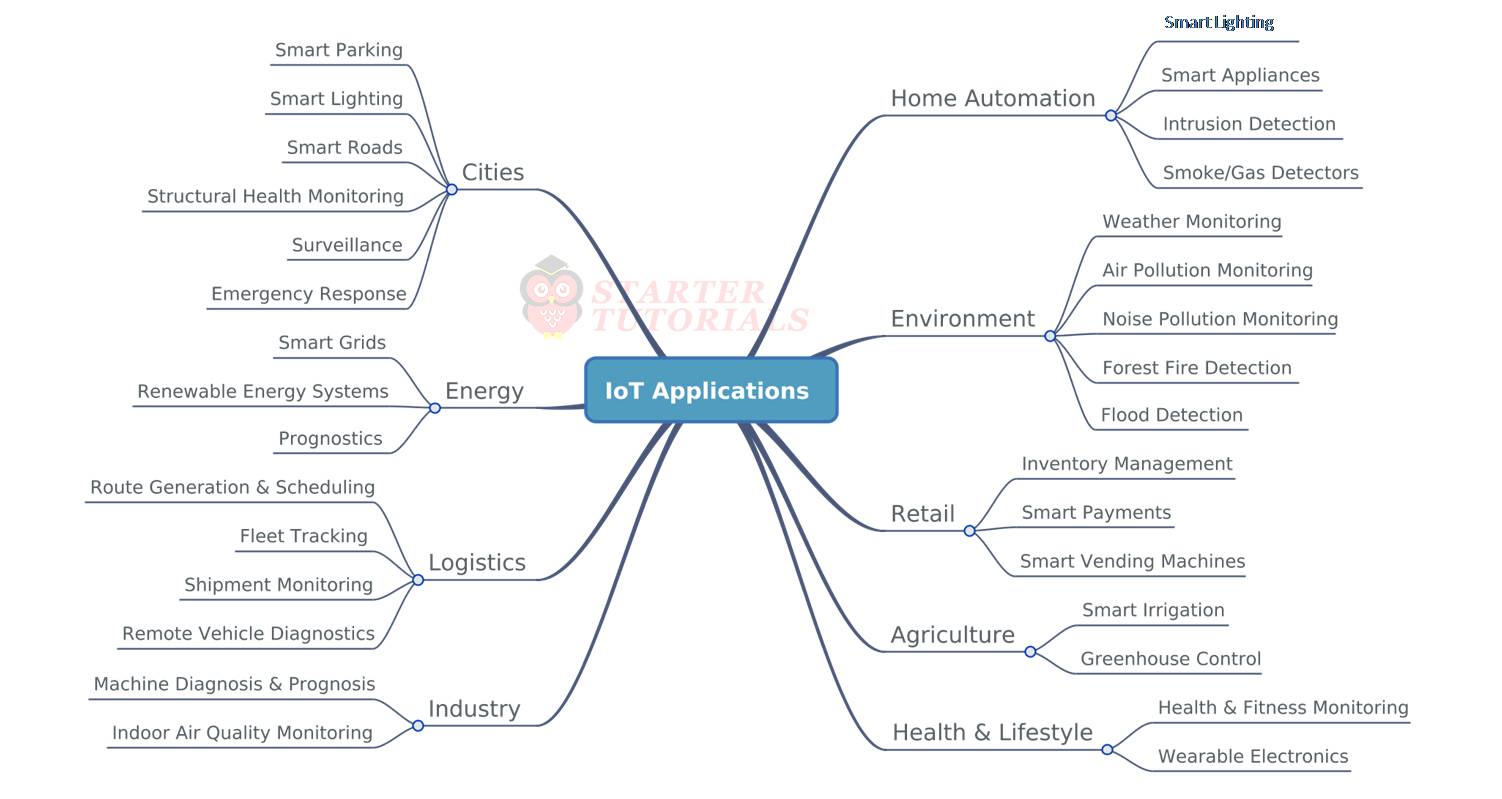
- Smart Homes: Devices like smart locks, thermostats, and cameras use SSH to secure communication with central hubs.
- Industrial IoT: Factories and warehouses rely on SSH to protect data transmitted between machines and monitoring systems.
- Healthcare: Wearable devices and medical equipment use SSH to ensure patient data remains confidential.
- Transportation: Autonomous vehicles and connected cars use SSH to secure communication with infrastructure and other vehicles.
These use cases highlight the versatility and importance of IoT SSH applications across various industries.
Challenges in Implementing IoT SSH Applications
Of course, nothing’s perfect. While IoT SSH applications offer a ton of benefits, there are some challenges to consider:
1. Complexity: Setting up SSH can be a bit of a headache, especially for businesses without dedicated IT teams. It requires careful configuration and management to ensure everything runs smoothly.
2. Resource Consumption: Encrypting and decrypting data can be resource-intensive, especially on smaller devices with limited processing power. This can lead to performance issues if not managed properly.
3. Key Management: Keeping track of public and private keys can be a logistical nightmare, especially in large-scale deployments. Mismanagement of keys can lead to security vulnerabilities.
Despite these challenges, the benefits of IoT SSH applications far outweigh the drawbacks. With the right planning and implementation, businesses can overcome these hurdles and create secure, scalable IoT ecosystems.
Solutions to Common Challenges
Luckily, there are solutions to these challenges. For example:
- Automated Key Management: Tools and platforms that automate the process of generating, distributing, and revoking keys can save businesses a ton of time and effort.
- Lightweight Protocols: Developers are working on creating more efficient versions of SSH that consume fewer resources, making them ideal for smaller devices.
- Training and Support: Providing employees with the knowledge and tools they need to properly implement and manage SSH can go a long way in ensuring success.
By addressing these challenges head-on, businesses can unlock the full potential of IoT SSH applications.
Best Practices for Using IoT SSH Applications
So, you’re ready to dive into the world of IoT SSH applications. Great! But before you do, here are some best practices to keep in mind:
1. Use Strong Authentication: Always use strong passwords and multi-factor authentication to protect your SSH keys. This adds an extra layer of security and makes it harder for attackers to gain access.
2. Regularly Update Keys: Just like passwords, SSH keys should be updated regularly to ensure they remain secure. This helps prevent key theft and unauthorized access.
3. Monitor Activity: Keep an eye on your SSH connections and look for any suspicious activity. Early detection can help you stop potential threats before they become major issues.
By following these best practices, you can ensure that your IoT SSH applications remain secure and effective.
Tools and Platforms for Managing IoT SSH Applications
There are plenty of tools and platforms out there to help you manage your IoT SSH applications. Some popular options include:
- OpenSSH: A free and open-source implementation of the SSH protocol that’s widely used across industries.
- SSH.com: A commercial platform that offers advanced features for managing large-scale SSH deployments.
- KeyCDN: A content delivery network that integrates SSH for secure data transfer.
These tools can help streamline the process of managing SSH keys, monitoring activity, and ensuring compliance with security standards.
Future Trends in IoT SSH Applications
Looking ahead, the future of IoT SSH applications is bright. Here are a few trends to watch out for:
1. Quantum-Resistant Encryption: As quantum computing becomes more prevalent, researchers are working on new encryption methods that can withstand quantum attacks. This could revolutionize how we approach IoT security in the future.
2. AI-Driven Security: Artificial intelligence is being used to enhance security by detecting and responding to threats in real-time. This could lead to smarter, more adaptive IoT SSH applications.
3. Edge Computing: By processing data closer to the source, edge computing can reduce latency and improve performance, making it an ideal partner for IoT SSH applications.
These trends highlight the exciting possibilities that lie ahead for IoT SSH applications. As technology continues to evolve, so too will the ways we use and secure connected devices.
Preparing for the Future
So, how can you prepare for these future trends? Start by staying informed about the latest developments in IoT and SSH technology. Attend conferences, read industry reports, and engage with experts in the field. By doing so, you’ll be better equipped to navigate the rapidly changing landscape of connected technology.
Conclusion
To sum it up, IoT SSH applications are a game-changer in the world of connected devices. They provide the security and functionality needed to build safe, scalable IoT ecosystems. From smart homes to industrial setups, these applications are transforming how we interact with technology in our daily lives.
But remember, with great power comes great responsibility. To fully harness the potential of IoT SSH applications, you need to be aware of the challenges and best practices involved. By doing so, you can create a secure, efficient, and future-proof IoT ecosystem.
So, what are you waiting for? Dive into the world of IoT SSH applications and start building the connected future you’ve always dreamed of. And don’t forget to share this article with your friends and colleagues—knowledge is power, after all!
Table of Contents
- What Are IoT SSH Applications?
- Why Are IoT SSH Applications Important?
- How Do IoT SSH Applications Work?
- Common Use Cases for IoT SSH Applications
- Challenges in Implementing IoT SSH Applications
- Solutions to Common Challenges
- Best Practices for Using IoT SSH Applications
- Tools and Platforms for Managing IoT SSH Applications
- Future Trends in IoT SSH Applications
- Preparing for the Future


Detail Author:
- Name : Veda Walker
- Username : joana88
- Email : mcglynn.hanna@hotmail.com
- Birthdate : 1977-12-14
- Address : 47870 Kianna Shoals Lake Lewishaven, RI 86577
- Phone : 754-267-2200
- Company : Grimes and Sons
- Job : Pewter Caster
- Bio : Saepe vel harum sapiente accusantium quas numquam ea. In laudantium ut repellat doloribus aut placeat. Consequuntur explicabo est sapiente optio nulla.
Socials
instagram:
- url : https://instagram.com/gerholdd
- username : gerholdd
- bio : Eum eius eum harum soluta. Praesentium animi doloremque dicta.
- followers : 4493
- following : 1295
facebook:
- url : https://facebook.com/donna_id
- username : donna_id
- bio : Nihil rem ut voluptatem et minima consectetur exercitationem.
- followers : 3389
- following : 60