AWS IoT Core SSH: The Ultimate Guide To Secure Shell Integration
Hey there, tech enthusiasts! If you're diving into the world of IoT (Internet of Things), you've probably stumbled upon AWS IoT Core. But what happens when you need to establish secure communication with your devices? That's where AWS IoT Core SSH comes into play. In this article, we'll explore how SSH can enhance your IoT setup, making it more secure and manageable. so buckle up, because we're about to take a deep dive into some serious tech talk!
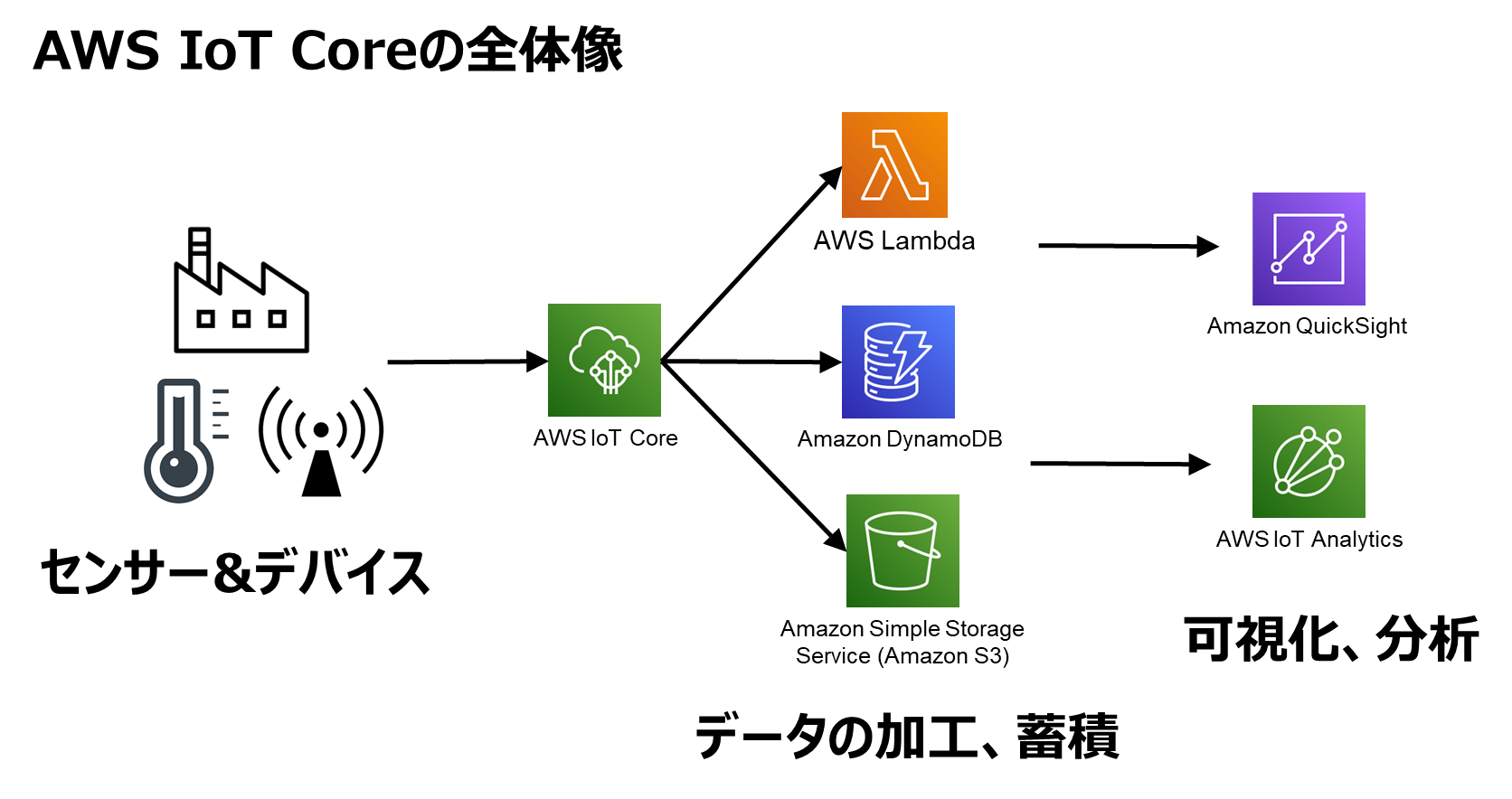
Now, let's break it down. AWS IoT Core is like the brain of your IoT operations. It handles all the heavy lifting—device management, data exchange, and communication. But what if you want to remotely access your devices for troubleshooting or configuration? Enter SSH. Secure Shell is like the Swiss Army knife for remote access, and integrating it with AWS IoT Core is a game-changer.
Throughout this article, we'll cover everything you need to know about AWS IoT Core SSH. From setting it up to troubleshooting common issues, we've got you covered. So whether you're a seasoned developer or just starting your IoT journey, this guide will help you level up your skills. Let's get started!
- Alive Rosenblum Leaks The Untold Story You Need To Know
- Alice Rosenum Leaks The Story Behind The Headlines
Table of Contents:
- What is AWS IoT Core SSH?
- Benefits of Using AWS IoT Core SSH
- Setting Up SSH with AWS IoT Core
- Security Best Practices for AWS IoT Core SSH
- Troubleshooting Common SSH Issues
- Real-World Use Cases for AWS IoT Core SSH
- Performance Optimization Tips
- Cost Considerations for AWS IoT Core SSH
- Comparison with Other Remote Access Tools
- Conclusion and Next Steps
What is AWS IoT Core SSH?
Alright, let's kick things off by answering the million-dollar question: What exactly is AWS IoT Core SSH? At its core (pun intended), AWS IoT Core SSH allows you to securely connect to IoT devices using the Secure Shell protocol. This means you can remotely manage and interact with your devices without compromising security.
Think of it this way: Imagine you have a fleet of IoT devices deployed across different locations. You need to update their firmware, troubleshoot issues, or monitor their performance. Instead of physically accessing each device, you can use SSH to do all of this remotely. AWS IoT Core SSH makes this process seamless and secure.
- Rory Mcilroy Relationship Timeline A Closer Look At His Love Story
- Chase My Mortgage A Comprehensive Guide To Tracking And Managing Your Home Loan
Here’s a quick breakdown of why AWS IoT Core SSH is such a big deal:
- It provides encrypted communication between your devices and the AWS cloud.
- It supports key-based authentication, adding an extra layer of security.
- It integrates with other AWS services, making it easier to manage your IoT ecosystem.
Why Choose AWS IoT Core SSH?
There are plenty of remote access tools out there, but AWS IoT Core SSH stands out for a few reasons. First, it's built specifically for IoT environments, meaning it's optimized for low-power devices with limited resources. Second, it leverages AWS's robust infrastructure, ensuring reliability and scalability. Finally, it integrates seamlessly with other AWS services, giving you a unified platform for managing your IoT operations.
Benefits of Using AWS IoT Core SSH
Now that we've established what AWS IoT Core SSH is, let's talk about why you should care. Here are some of the key benefits:
- Enhanced Security: SSH uses encryption and key-based authentication to ensure secure communication.
- Remote Access: You can manage your IoT devices from anywhere, as long as you have an internet connection.
- Scalability: AWS IoT Core SSH can handle thousands of devices without breaking a sweat.
- Integration: It works seamlessly with other AWS services, such as AWS Lambda and Amazon S3.
Let's dive deeper into the security aspect. With SSH, you don't have to worry about unauthorized access to your devices. The protocol uses public-key cryptography to authenticate users, meaning only those with the correct private key can gain access. This is especially important in IoT environments, where devices are often deployed in unsecured locations.
Setting Up SSH with AWS IoT Core
Ready to get your hands dirty? Setting up SSH with AWS IoT Core is surprisingly straightforward. Here's a step-by-step guide to help you get started:
- Create an IAM Role: Start by creating an IAM role with the necessary permissions for SSH access.
- Configure Device Shadow: Use AWS IoT Device Shadow to manage the state of your devices.
- Set Up Key Pairs: Generate SSH key pairs and distribute the public keys to your devices.
- Test the Connection: Use an SSH client to test the connection to your device.
Pro tip: Always test your setup in a staging environment before deploying it to production. This will help you catch any issues before they become major headaches.
Best Practices for Configuration
When setting up SSH with AWS IoT Core, there are a few best practices you should keep in mind:
- Use strong, unique passwords for your SSH keys.
- Limit access to only trusted IP addresses.
- Regularly update your devices' firmware to patch security vulnerabilities.
Security Best Practices for AWS IoT Core SSH
Security should always be top of mind when working with IoT devices. Here are some best practices to keep your AWS IoT Core SSH setup secure:
- Use Strong Authentication: Always use key-based authentication instead of password-based authentication.
- Enable Firewall Rules: Configure firewall rules to restrict access to only authorized devices.
- Monitor Activity: Use AWS CloudTrail to monitor SSH activity and detect any suspicious behavior.
Remember, security is a continuous process. Regularly review your setup and update your security measures as needed.
Troubleshooting Common SSH Issues
Even with the best setup, things can go wrong. Here are some common SSH issues you might encounter and how to fix them:
- Connection Timeout: Check your firewall rules and ensure the device is reachable over the network.
- Authentication Failed: Verify that you're using the correct private key and that the public key is correctly installed on the device.
- Permission Denied: Make sure the user has the necessary permissions to access the device.
If you're still stuck, don't hesitate to reach out to the AWS support team. They're always happy to help!
Debugging Tips
Here are a few debugging tips to help you troubleshoot SSH issues:
- Use the
ssh -vcommand to get detailed logs and identify the issue. - Check the device's SSH server logs for any errors or warnings.
- Test the connection from a different network to rule out network-related issues.
Real-World Use Cases for AWS IoT Core SSH
Now that we've covered the technical aspects, let's talk about some real-world use cases for AWS IoT Core SSH:
- Remote Device Management: Use SSH to remotely manage and configure IoT devices deployed in remote locations.
- Firmware Updates: Push firmware updates to your devices without physically accessing them.
- Monitoring and Diagnostics: Use SSH to monitor device performance and diagnose issues in real-time.
These use cases highlight the versatility and power of AWS IoT Core SSH. Whether you're managing a small fleet of devices or a large-scale IoT deployment, SSH can help you stay in control.
Performance Optimization Tips
Performance is key when working with IoT devices. Here are some tips to optimize the performance of your AWS IoT Core SSH setup:
- Use Compression: Enable SSH compression to reduce the amount of data transmitted over the network.
- Limit Connections: Restrict the number of concurrent SSH connections to avoid overwhelming your devices.
- Monitor Resource Usage: Keep an eye on CPU and memory usage to ensure your devices aren't running out of resources.
By following these tips, you can ensure your AWS IoT Core SSH setup runs smoothly and efficiently.
Cost Considerations for AWS IoT Core SSH
Cost is always a consideration when working with cloud services. Here's what you need to know about the cost of using AWS IoT Core SSH:
AWS IoT Core is billed based on the number of messages processed and the number of devices connected. SSH itself doesn't incur additional costs, but you may incur costs for other AWS services you use in conjunction with it, such as AWS Lambda or Amazon S3.
To keep costs under control, monitor your usage closely and optimize your setup to minimize unnecessary resource consumption.
Comparison with Other Remote Access Tools
There are plenty of remote access tools out there, but AWS IoT Core SSH has a few advantages:
- Integration: It integrates seamlessly with other AWS services, making it easier to manage your IoT ecosystem.
- Scalability: It can handle thousands of devices without breaking a sweat.
- Security: It uses encryption and key-based authentication to ensure secure communication.
That said, other tools like TeamViewer or AnyDesk may be better suited for certain use cases. It all depends on your specific needs and requirements.
Conclusion and Next Steps
And there you have it—a comprehensive guide to AWS IoT Core SSH. From setting it up to troubleshooting common issues, we've covered everything you need to know to get started. So what's next? Here are a few suggestions:
- Start experimenting with AWS IoT Core SSH in your own projects.
- Explore other AWS services that can enhance your IoT setup.
- Stay up-to-date with the latest trends and developments in the IoT space.
Remember, the world of IoT is constantly evolving, and staying ahead of the curve is key to success. If you found this article helpful, don't forget to share it with your friends and colleagues. And as always, feel free to leave a comment or question below. Happy coding!


Detail Author:
- Name : Patience Greenfelder
- Username : chester.zemlak
- Email : maegan38@hintz.info
- Birthdate : 1973-05-07
- Address : 457 Hansen Way Eleazarbury, OK 89759
- Phone : +1-562-669-1868
- Company : Nicolas Ltd
- Job : Tree Trimmer
- Bio : Sed suscipit eos amet vero at eligendi. Aut iusto quisquam distinctio voluptates at et molestias dignissimos. Ut omnis optio eum repudiandae modi animi. Mollitia et quo eos fugit ipsam aut.
Socials
linkedin:
- url : https://linkedin.com/in/rickcrona
- username : rickcrona
- bio : Aut distinctio et enim molestiae.
- followers : 5895
- following : 2772
twitter:
- url : https://twitter.com/rick2002
- username : rick2002
- bio : Quia expedita dicta alias tempora laboriosam excepturi. Commodi veritatis praesentium quis fuga. Possimus autem autem neque laborum laborum.
- followers : 5611
- following : 1797
tiktok:
- url : https://tiktok.com/@rick_official
- username : rick_official
- bio : Vero aliquam officiis quo assumenda maxime. Explicabo unde modi omnis ex nam.
- followers : 4453
- following : 604
instagram:
- url : https://instagram.com/rcrona
- username : rcrona
- bio : Tenetur cumque ab quisquam et nihil eum aut. Et nulla dolor placeat ut aut aut eos.
- followers : 3176
- following : 730